Disabling SMB on Windows
This article describes how to disable Server Message Block (SMB) version 1 (SMBv1), SMB version 2 (SMBv2), and SMB version 3 (SMBv3) on SMB client and server components.
SMBv1 has significant security vulnerabilities, and we strongly encourage you not to use it. SMBv1 isn’t installed by default in any edition of Windows 11 or Windows Server 2019 and later versions. SMBv1 also isn’t installed by default in Windows 10, except Home and Pro editions. We recommend that instead of reinstalling SMBv1, you update the SMB server that still requires it.
What is Microsoft SMB Protocol and CIFS Protocol?
The Server Message Block (SMB) Protocol is a network file sharing protocol, and as implemented in Microsoft Windows is known as Microsoft SMB Protocol. The set of message packets that defines a particular version of the protocol is called a dialect. The Common Internet File System (CIFS) Protocol is a dialect of SMB. Both SMB and CIFS are also available on VMS, several versions of Unix, and other operating systems.
To learn more go to https://learn.microsoft.com/en-us/windows/win32/fileio/microsoft-smb-protocol-and-cifs-protocol-overview
Why disabling SMB on Microsoft Windows is important?
Disabling SMB (Server Message Block), especially older versions like SMBv1, in Microsoft Windows is important for security reasons. Here’s a breakdown of why it matters:
1. SMBv1 is Outdated and Insecure
- SMBv1, introduced in the 1980s, lacks modern security features.
- It does not support encryption, integrity checks, or secure negotiation.
- WannaCry ransomware (2017) and other major attacks exploited SMBv1 vulnerabilities to spread rapidly.
2. Vulnerable to Remote Code Execution (RCE)
- SMB vulnerabilities have been used by hackers to execute malicious code remotely without authentication.
- Examples:
- EternalBlue exploit (used in WannaCry and NotPetya)
- Various CVE-listed vulnerabilities over the years.
3. Minimizing Attack Surface
- Disabling unused protocols reduces the number of entry points for attackers.
- If SMB (especially SMBv1) is not needed, it’s better to disable it to prevent exploitation.
4. Compliance and Best Practices
- Disabling insecure protocols like SMBv1 is often a requirement for:
- Security audits
- Regulatory compliance (e.g., PCI-DSS, HIPAA)
- Microsoft itself strongly recommends disabling SMBv1.
5. Modern Alternatives Exist
- SMBv2 and SMBv3 offer:
- Encryption
- Improved performance
- Security features like signing
- Unless legacy systems require SMBv1, it should be disabled.
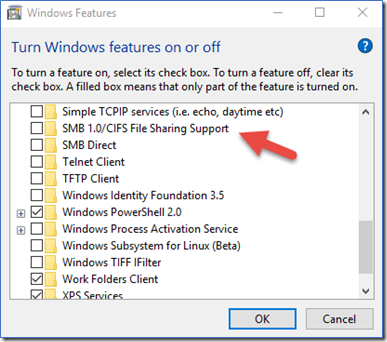
How to Disable SMB on Windows Clients
Via Windows Features GUI: Control Panel -> Programs -> Turn Windows features on or off -> Uncheck “SMB 1.0/CIFS File Sharing Support”